Setup SeekTable for secure embedding
You can embed SeekTable reports into your web application in a secure way by enabling JWT-based authentication for published reports or read-only app view. Secure embedding is available only for self-hosted SeekTable (or managed instance) and only for user accounts with Advanced Publishing subscription. How it works:
|
Your web app
Generates secure JSON Web Token |
→
|
Secure report link
JWT is passed to SeekTable report as an URL parameter or cookie |
→
|
SeekTable
Decodes/verifies JWT and applies claims as report parameters. |
JWT lifetime can be is limited by its expiration date. JWT claims (payload) may be contain report parameters and in this way you can organize row-level security for embedded reports (without SSO): each 'main' app user may have its own set of parameters that restrict access to the data. Users cannot change these parameters because their JWT tokens are signed with a secret key. JWT tokens may be encrypted with symmetric algorithm, and in this case even values of parameters passed in JWT are secured (cannot be accessed by end-users).
If you want to evaluate this feature before purchase you can request a free 14-day trial.
How to enable JWT-based auth for embedded SeekTable views:
Step 1: Configure SeekTable JWT validation for published reports
Find docker-compose.seektable.env file and add the following lines:
SeekTable_ST__PublicReport__AuthJwtUrlParameter=auth SeekTable_ST__PublicReport__AuthJwtCookieName=cookie_name_or_empty_if_not_used SeekTable_ST__PublicReport__AuthJwt__ValidIssuer=your_web_app_issuer_value SeekTable_ST__PublicReport__AuthJwt__ValidateIssuer=true SeekTable_ST__PublicReport__AuthJwt__ValidateAudience=false SeekTable_ST__PublicReport__AuthJwt__ValidateLifetime=true SeekTable_ST__PublicReport__AuthJwt__ValidateIssuerSigningKey=true SeekTable_ST__PublicReport__AuthJwt__IssuerSigningKeyString=your_secret_signing_key_min_32_chars
To ensure the key's value is passed to SeekTable without modification, it is recommended to restrict its contents to English letters and digits
(a known issue when a key value contains -). If your key must contain special symbols use SeekTable_ST__PublicReport__AuthJwt__IssuerSigningKeyBase64String app setting instead (this should be a BASE64 encoded value of key's bytes).
If you want enable JWT encryption add:
SeekTable_ST__PublicReport__AuthJwt__TokenDecryptionKeyString=your_secret_decryption_key_min_32_chars
Similar to the signing key: use English letters and digits or use
SeekTable_ST__PublicReport__AuthJwt__TokenDecryptionKeyBase64String to specify BASE64-encoded key bytes.
If you want enable generate embed token API add:
SeekTable_ST__PublicReport__EnableGenerateEmbedToken=true
Then re-create seektable/seektable docker container (this is performed automatically if you use docker compose up to start the containers).
Now you should see Security tab on "Configure Published Report" form:
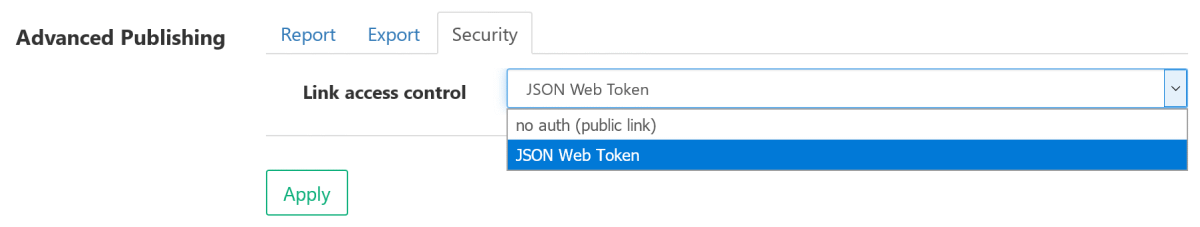
Step 2: Generate JWT to access secured published reports
You can either use generate embed token API to obtain JWT or generate JWT on your application side (recommended).
The following code snippets illustrate how to generate JSON Web Token for embeds:
// nuget package: System.IdentityModel.Tokens.Jwt
var handler = new JwtSecurityTokenHandler();
var signingCredentials = new SigningCredentials(
new SymmetricSecurityKey(System.Text.Encoding.UTF8.GetBytes("your_secret_signing_key_min_16_chars")),
SecurityAlgorithms.HmacSha256Signature);
var token = handler.CreateJwtSecurityToken(
subject: new ClaimsIdentity(new[] { new Claim("report_param_name", "report_param_val") }),
signingCredentials: signingCredentials,
audience: "",
issuer: "your_web_app_issuer_value",
expires: DateTime.UtcNow.AddMinutes(5)); // 5 mins expiration
var jwt = handler.WriteToken(token);
// nuget package: System.IdentityModel.Tokens.Jwt
var handler = new JwtSecurityTokenHandler();
var signingCredentials = new SigningCredentials(
new SymmetricSecurityKey(System.Text.Encoding.UTF8.GetBytes("your_secret_signing_key_min_16_chars")),
SecurityAlgorithms.HmacSha256Signature);
var encryptCredentials = new EncryptingCredentials(
new SymmetricSecurityKey(System.Text.Encoding.UTF8.GetBytes("your_secret_decryption_key_min_16_chars")),
SecurityAlgorithms.Aes128KW,
SecurityAlgorithms.Aes128CbcHmacSha256);
var tokenDescriptor = new SecurityTokenDescriptor {
Audience = "",
Issuer = "your_web_app_issuer_value",
Subject = new ClaimsIdentity(new[] { new Claim("report_param_name", "report_param_val") }),
Expires = DateTime.UtcNow.AddMinutes(5), // 5 mins expiration
EncryptingCredentials = encryptCredentials,
SigningCredentials = signingCredentials
};
var encryptedJwt = handler.CreateEncodedJwt(tokenDescriptor);
// module: jsonwebtoken
var jwt = require("jsonwebtoken");
var expiresInMins = 5;
var payload = {
report_param_name: "report_param_value",
iss: "your_web_app_issuer_value",
exp: Math.round(Date.now() / 1000) + (expiresInMins * 60)
};
var token = jwt.sign(payload, "your_secret_signing_key_min_16_chars");
# package: PyJWT
import jwt
import time
payload = {
"report_param_name": "report_param_value",
"iss": "your_web_app_issuer_value",
"exp": round(time.time()) + (60 * 5) # 5 mins expiration
}
token = jwt.encode(payload, "your_secret_signing_key_min_16_chars", algorithm="HS256")
require_once "./vendor/firebase-php-jwt/JWT.php";
use \Firebase\JWT\JWT;
$jwtSigningKeyStr = "your_secret_signing_key_min_16_chars";
$jwtIssuer = "your_web_app_issuer_value";
$payload = [
"report_param_name" => "report_param_value",
"iss" => $jwtIssuer,
"exp" => strtotime("+5 minutes")
];
$token = JWT::encode($payload, $jwtSigningKeyStr);
How to pass a multivalue parameter?
On SeekTable side JWT payload claim values are mapped to System.Security.Claims.Claim objects where Value is always converted to a string.
As a result, it is not possible to provide multiple values simply by specifying a JSON array as a claim value. To overcome this limitation the following workaround may be used:
- Serialize a JSON array into a string and use this string as a claim value.
SeekTable identifies string values wrapped in brackets (e.g.,
[1,2,3]) and automatically attempts to deserialize them as JSON arrays. -
Alternatively, you may pass multiple values as a comma or semicolon (or any other separator) string, something like
value,value2,value3.
Then, in the cube configuration configure an Expression for the multi-value parameter that comes from JWT (let's assume that multi-value parameter's Name is 'param_name'):
Parameter["param_name"]!=null && Parameter["param_name"].Length==1 && Parameter["param_name"][0].ToString().Contains(",") ? String.Split(",", Parameter["param_name"][0]) : Parameter["param_name"]
The idea is to split a single string value if it contains a separator.
If you don't use C#/.NET please check your development platform about how to generate JSON Web Token. Notes:
- signing should use symmetric algorithm
- encryption should use symmetric algorithm
- key length should be at least 16 bytes
Step 3: Pass JWT to embedded SeekTable report
There are 2 ways how you can pass generated JWT to the report embedded with IFRAME:
- as an URL parameter (parameter name is configured by
SeekTable_ST__PublicReport__AuthJwtUrlParametersetting) - as a cookie (cookie name is configured by
SeekTable_ST__PublicReport__AuthJwtCookieName)
This approach is possible only if self-hosted SeekTable is accessed as a sub-domain of your main web application.
Important notes:
- JWT authorization is used only for published reports where Link access control is set to JSON Web Token.
- Owner of published report always can view it (when logged in), even without JWT or if JWT is invalid. It is recommended to test secure published reports in another browser session (incognito/private window).
Restrict JWT access
You can generate a scoped JWT to grant access to only the concrete report or dashboard. To do that add
seektable_report_id into JWT payload, for example (C#):
new Claim("seektable_report_id", "public_link_id")
Embedded app view
If you want to offer to users of your app a higher level of reports interactivity and allow them to make ad-hoc queries you can embed SeekTable's "app" view (read-only access to some user account) - to get the point just imagine that whole demo.seektable.com view is embedded (without top-menu):
Technically this works in this way:
- on your self-hosted SeekTable installation you can create an 'embedded' user account (or several ones) with cubes / reports that you want to expose inside your main web application
This user account should have Advanced Publishing capability. - your main app generates a JWT as described above (for embedded reports) + adds a special claim
seektable_user_emailwith a login email of 'embedded' SeekTable user account. This JWT may contain additional name-value pairs to override appropriate report parameters (end-users will not be able to change these report parameters). - add to your app an iFrame with your SeekTable installation URL + pass generated JWT with an URL parameter (
auth) or a cookie. This URL can be just a base URL (to show default account's screen with list of cubes) or this may be an URL of the concrete report. - embedded app view is a read-only by default: end-users can view existing reports, change report options and even create new reports, but any modifications cannot be saved.
However, it is possible to allow saving modifications by adding
seektable_user_readonly=falseinto JWT's payload. - any mentions of SeekTable (and the footer-line) can be removed with white-label mode capability.
White-labelling makes possible to customize app's CSS styles (colors, fonts etc) and UI labels; for instance, you can rename "Cubes" to "Datasets".
When installation has activated "white-label mode" JWT can containseektable_app_page_css_classclaim to apply any custom CSS class to app's page<body>tag: in this way CSS styles can be customized only for this concrete embedding (you can add your own custom app's CSS styles).
You can use some predefined CSS classes to customize embedded app view:- no-left-menu
- if you want to show only a concrete report and do not allow end-users to navigate via left menu.
- st-checkbox-classic
- force classic HTML checkboxes instead of switches.
- st-tabs-classic
- force classic tabs design instead of material-like style.
- SeekTable app supports light/dark color themes.
By default embedded app view uses light theme; host app can control this option by
specifying
seektable_user_themeJWT claim (possible values are: "light", "dark" and "auto").